Configure SAML with Microsoft Entra ID¶
This page explains how to integrate Microsoft Entra ID (Azure AD) as a SAML Identity Provider to authenticate your users on Reemo.
Important
This feature is available starting from the Enterprise plan.
Note
Configure SAML in Reemo¶
Access Connectors in the instance Admin Area.¶
Configure SAML in Organization > Connectors.¶
Create the SAML Connector in Reemo¶
Create a new Connector of type SAML Connector.
Fill in the basic fields:
Friendly Name: name displayed to your users (e.g., EntraID).
Issuer / App URI ID:
reemo.The other fields (Entry Point, Federation XML) will be completed after configuring Entra ID.
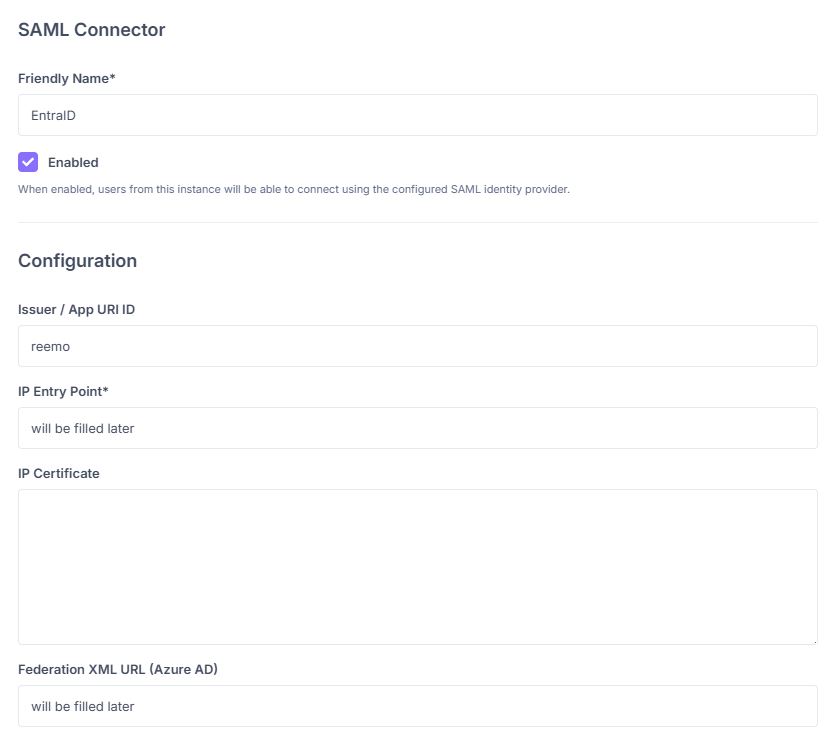
Fill in the basic fields of the SAML connector.¶
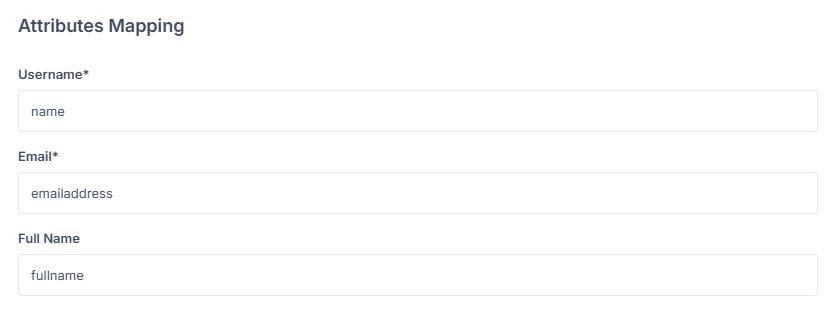
Configure Attributes.¶
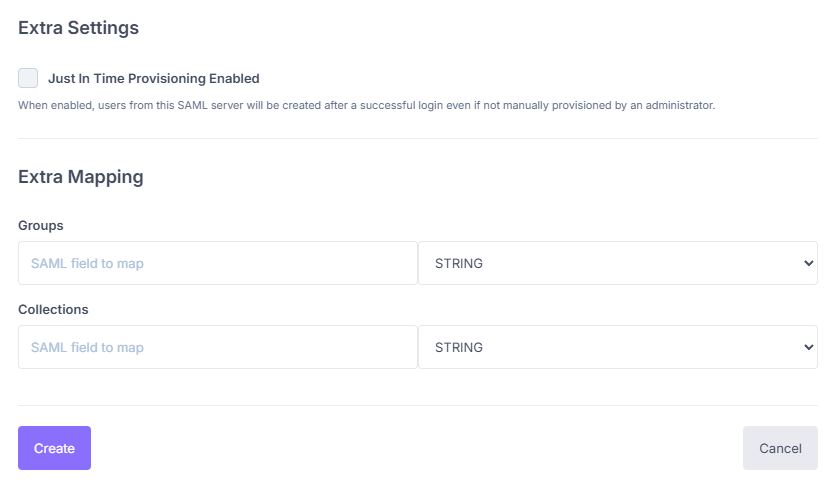
Create the connector¶
3) Validate to generate the connector’s Callback URL. You will need this in EntraID (Single sign-on URL).
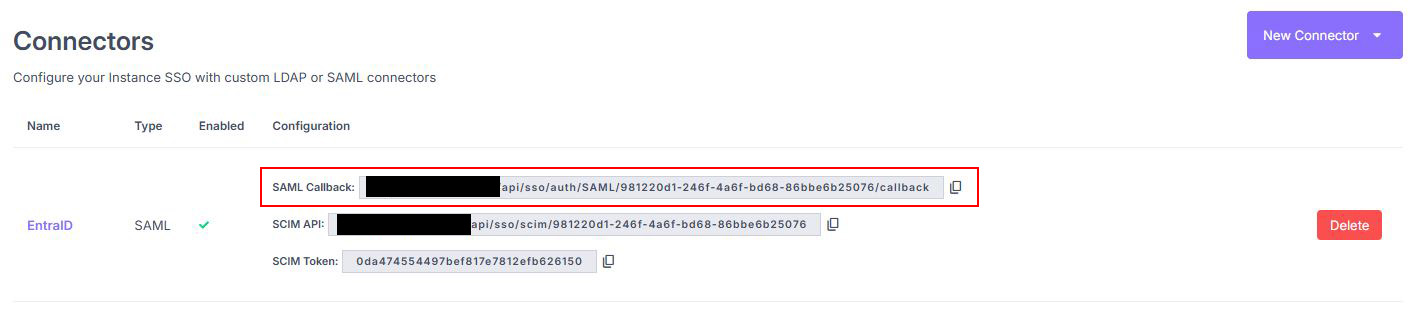
Copy the Callback URL generated by the SAML connector.¶
Configure the SAML Application in Entra ID¶
Log in to the EntraID portal: https://portal.azure.com
Create a new application: Microsoft Entra ID > Manage > Enterprise applications > New application.
- Click Create your own application.
Give it a name (e.g., Reemo).
Choose Integrate any other application you don’t find in the gallery (Non-gallery).
Click Create.
Open the application and go to Single sign-on > select SAML.
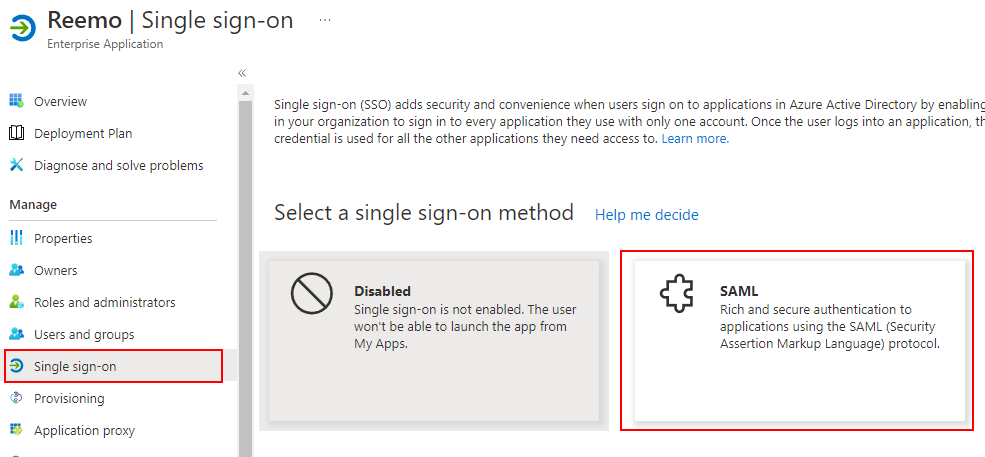
Choose SAML as the Single Sign-On method.¶
In the Set up [app name] section:
Copy the Login URL and paste it into IdP Entry Point in Reemo.
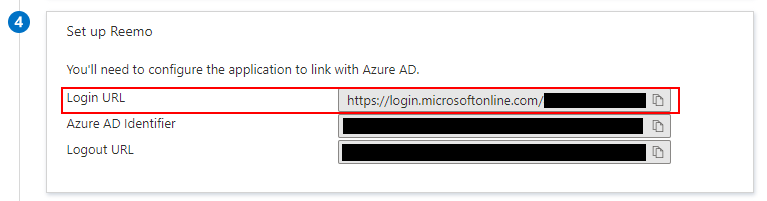
Copy the Login URL into the IdP Entry Point field.¶
In the SAML Certificates section:
Copy the federationmetadata.xml URL from the App Federation Metadata URL.
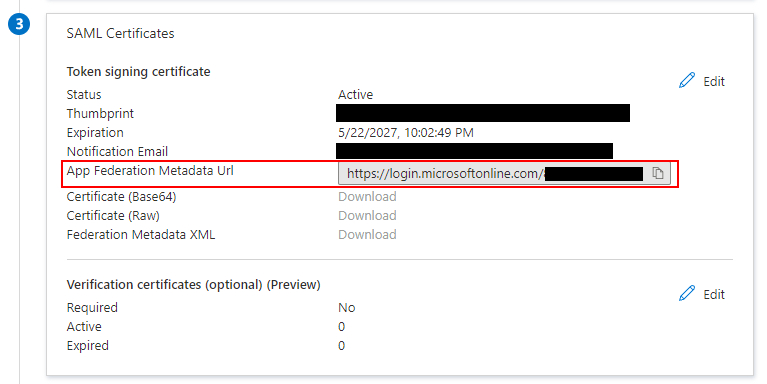
Copy the federationmetadata.xml URL.¶
Paste it into the Federation XML URL field of the Reemo connector.
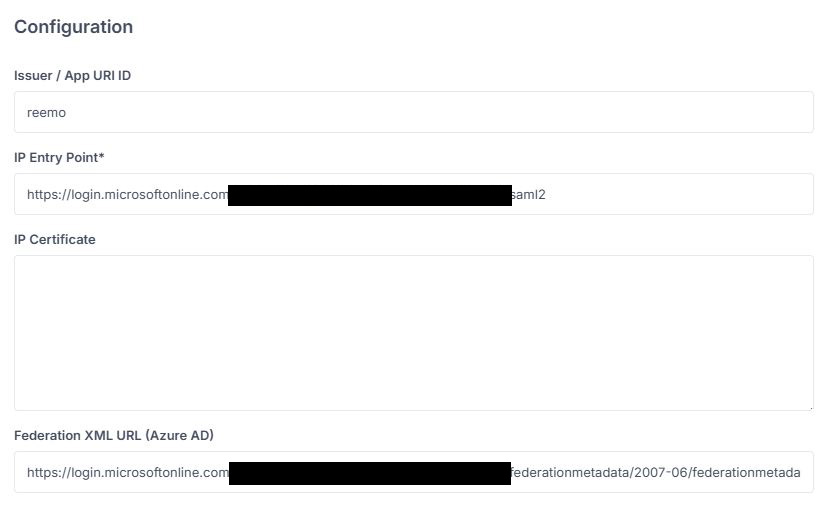
Fill the fields left to be filled previously¶
Configure Attributes (Attribute Statements)¶
Map the attributes so that Reemo receives the correct information from Entra ID:
Username →
nameEmail →
emailaddressFull Name →
displayname
Configure the Identifier and Reply URL¶
To finish the configuration, Entra requires setting up the Identifier and Reply URL (Assertion Consumer Service URL):
In the Basic SAML Configuration section, click Edit.
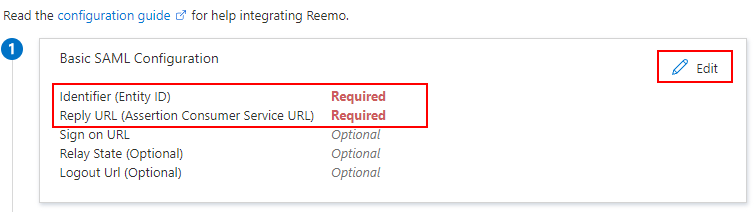
Click Edit to modify the Basic SAML configuration.¶
Add an Identifier: use the value defined in Reemo (
reemo).Add a Reply URL: use the Callback URL generated by the connector in Reemo.
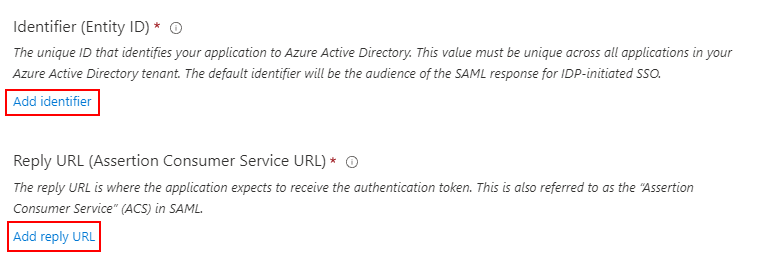
Add an Identifier and a Reply URL with the values from Reemo.¶
Click Save, then use the Test button to verify the configuration.
Note
The connector’s Callback URL is visible in the connector list, under the Configuration column.
Provision Users¶
There are two approaches to grant SSO access to users.
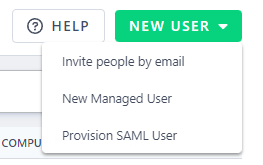
Provision SAML users directly in the organization.¶
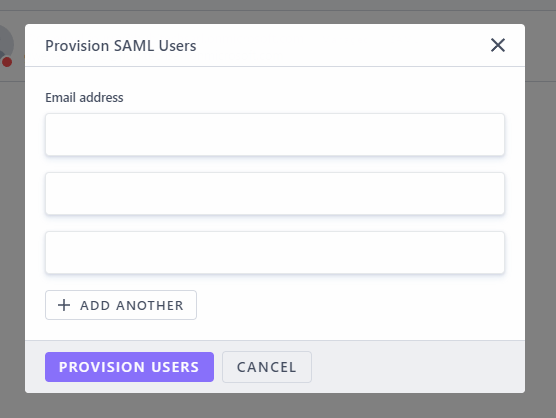
Add users by email through the provisioning popup.¶
In the Entra portal, open the Reemo application.
Go to Provisioning > Get Started.
Set Provisioning Mode to Automatic.
- Fill in:
Tenant URL: SCIM API value provided by Reemo (in the connector list).
Secret Token: SCIM Token value provided by Reemo.
Click Test Connection, then Save.
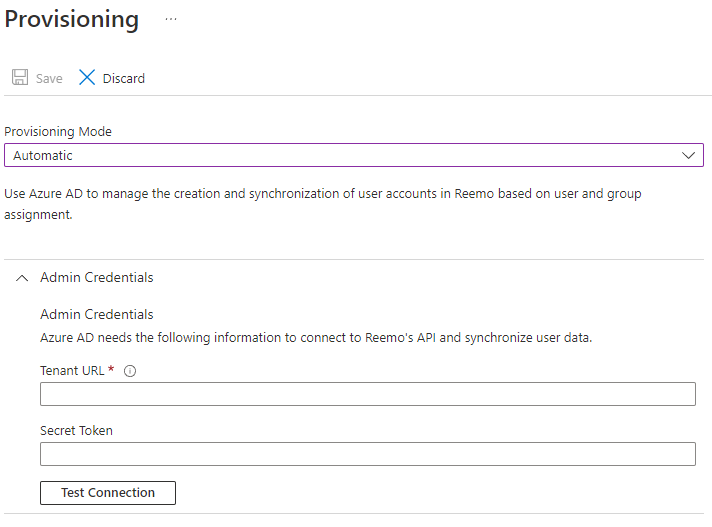
Automate user provisioning with SCIM.¶
You should now be able to provision users from Microsoft Entra ID using the provisioning interface.
Sign in via SAML¶
Once the connector is active and users are provisioned (or JIT enabled), they can sign in:
General portal access (Private Cloud / On-Prem):
https://[portal_url]/
Direct access to the organization (Public Cloud):
https://[portal_url]/login/[organization_shortname]
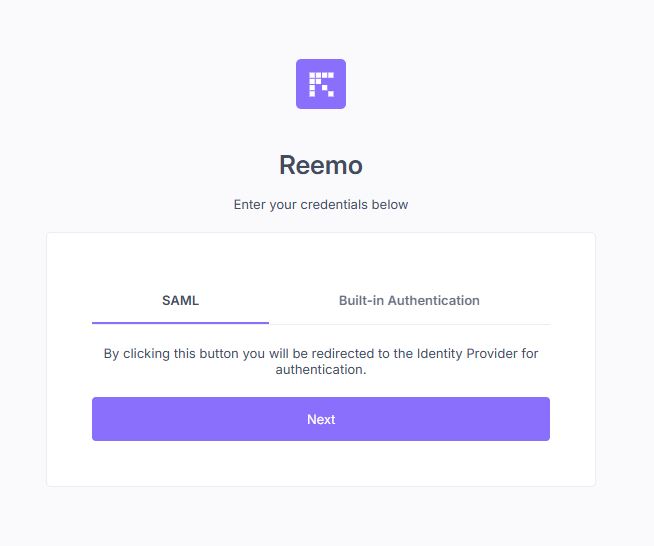
Select SAML and click Next to be redirected to Microsoft Entra ID.¶