Security Settings¶
The Security section of the organization allows you to configure and strengthen the security rules applied to all users and resources (computers, containers). These settings are defined at the global organization level and apply to all members.
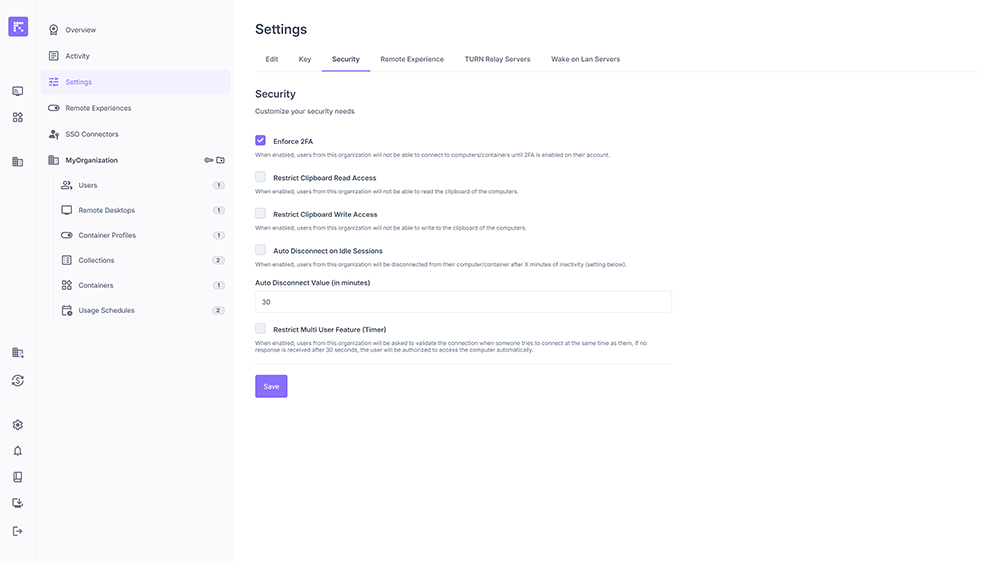
Organization security settings page.¶
Available Options¶
Enforce 2FA¶
Enables mandatory two-factor authentication (2FA) for all organization users.
As long as 2FA is not enabled on their account, users cannot connect to computers or containers.
Recommended to comply with security best practices (stronger protection against credential theft).
Restrict Clipboard Read Access¶
Blocks the ability for users to read the clipboard of a remote computer or container.
Useful to prevent sensitive data leaks copied from a machine.
Restrict Clipboard Write Access¶
Blocks the ability for users to write into the clipboard of a remote computer or container.
Recommended if you want to prevent files or text from outside the secure environment being transferred to the remote machine.
Auto Disconnect on Idle Sessions¶
Automatically disconnects users in case of prolonged inactivity.
This option reduces risks associated with an unattended open session (e.g. a user forgets to log out).
Auto Disconnect Value (in minutes)¶
Defines the inactivity period (in minutes) before automatic disconnection applies.
Example: with a value of 30, the user is disconnected after 30 minutes without activity.
Restrict Multi User Feature (Timer)¶
When another user tries to connect to a computer/container already in use, a confirmation message is displayed to the current session user.
That user must confirm whether to allow the simultaneous connection.
If no response is given within 30 seconds, access is automatically granted to the second user.
This mechanism makes it possible to:
control concurrent access to machines,
avoid blocking a user from joining a session,
maintain productivity while keeping a level of human validation.
Best Practices¶
Always enable 2FA: this is the most critical security measure.
Restrict clipboard access in sensitive or regulated environments (e.g. production data, financial environments).
Configure auto-disconnect according to context: 15 minutes for critical environments, 30 minutes or more for standard use.
Limit multi-user sessions in environments where confidentiality is a priority (e.g. audit, finance).