Container Providers¶
A Container Provider is an integration that allows you to manage container environments (e.g., Docker Swarm, Kubernetes) within the platform. It centralizes configuration, certificates, secrets, and images to simplify deployment and operations.
Note
When a Container Provider is created in Reemo, it is disabled by default and must be explicitly enabled by an instance administrator.
Overview¶
The Container Providers list displays:
Name: identifier chosen by the administrator.
Type: technology used (e.g., SWARM).
Multi-cluster: deployment across one or more clusters.
Visibility: Public or Private.
State: Enabled or Disabled.
Test: connectivity validation button.
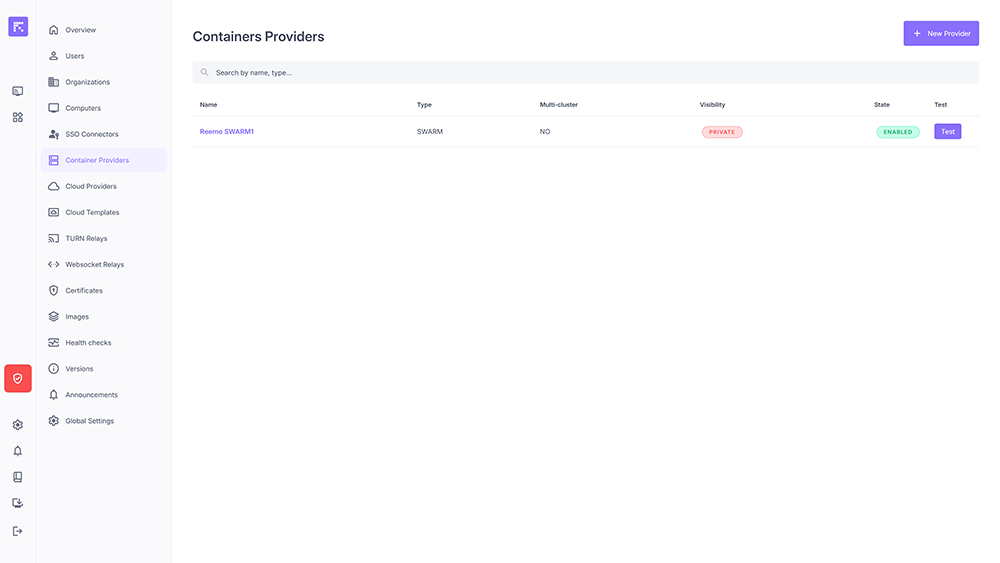
List of Container Providers¶
Creating a Container Provider¶
Click New Provider.
Fill in the fields:
Name: provider name.
Type: choose SWARM or KUBERNETES.
Visibility: Public or Private.
Multi-cluster deployment: enable or disable multi-cluster management (Active/Passive or Active/Active).
Comments: administrative notes.
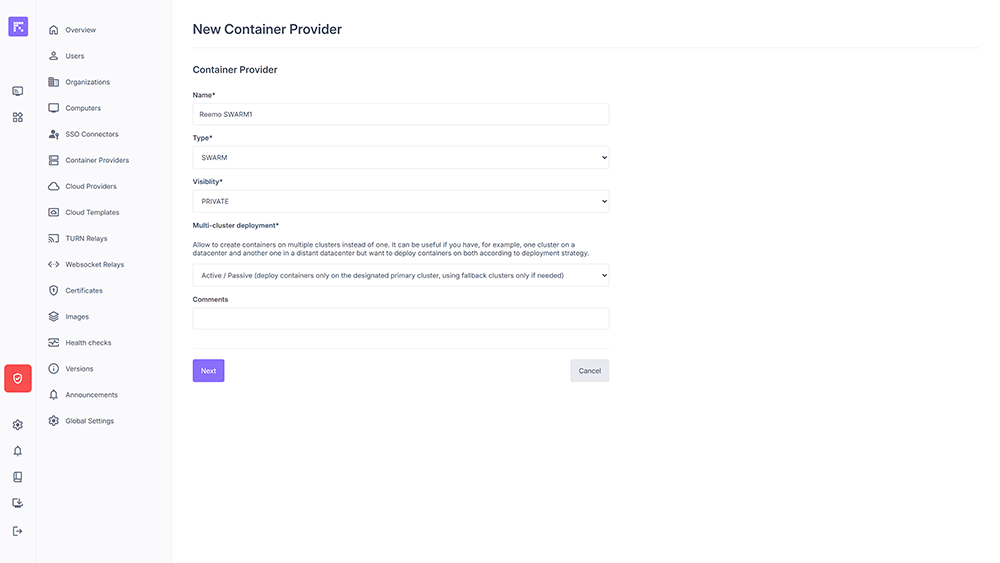
Container Provider creation form¶
Example of cluster configurations:
You can deploy containers on a simple cluster or using a multi-cluster configuration. A multi-cluster configuration allows to create containers on multiple clusters instead of one. It can be useful if you have, for example, one cluster on a datacenter and another one in a distant datacenter but want to deploy containers on both according to deployment strategy.
Simple cluster: Deploy containers only on this cluster.
Multi-cluster Active/Passive: Deploy containers only on the designated primary cluster, using the other clusters as a fallback if needed.
Multi-cluster Active/Active: Deploy containers randomly across multiple clusters.
URL: API access point of the cluster. It can be an internal address or a public DNS name. In the latter case, an Ansible installation of the infrastructure will be required.
Server Name (SNI): optional field corresponding to the Common Name of the provider environment SSL certificate.
Cert Auth: enables certificate-based authentication, if required.
- Certificate:
Use an Existing Certificate: allows selecting an existing certificate from the Certificates module.
Specify a certificate: allows manually entering the KEY, CERT, and CA contents.
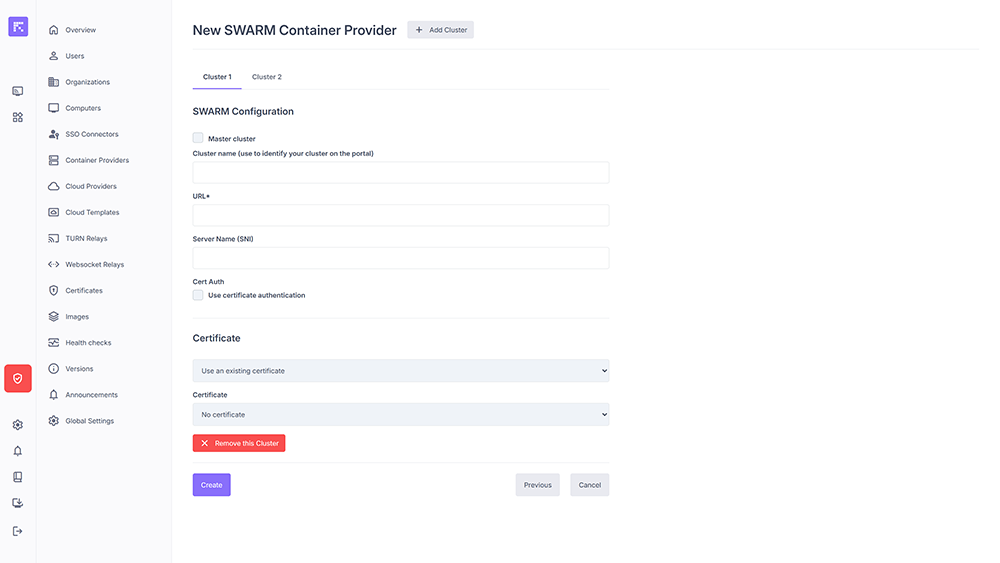
Example of a SWARM cluster configuration¶
Add Cluster: allows adding a new cluster to the provider (option available only if multi-cluster mode is enabled).
Master cluster: field visible only when Active/Passive multi-cluster mode is enabled. It defines the main (master) cluster used for deployments. Other clusters will be considered secondary (fallback) and used only if the main cluster is unavailable.
Cluster name: internal identifier of the cluster (visible only if multi-cluster mode is enabled).
URL: API access point of the cluster. It can be an internal address or a public DNS name. In the latter case, an Ansible installation of the infrastructure will be required.
Server Name (SNI): optional field corresponding to the Common Name of the provider environment SSL certificate.
Cert Auth: enables certificate-based authentication, if required.
- Certificate:
Use an Existing Certificate: allows selecting an existing certificate from the Certificates module.
Specify a certificate: allows manually entering the KEY, CERT, and CA contents.
Remove the Cluster: removes the cluster (option available only if multi-cluster mode is enabled and at least 2 clusters are configured).
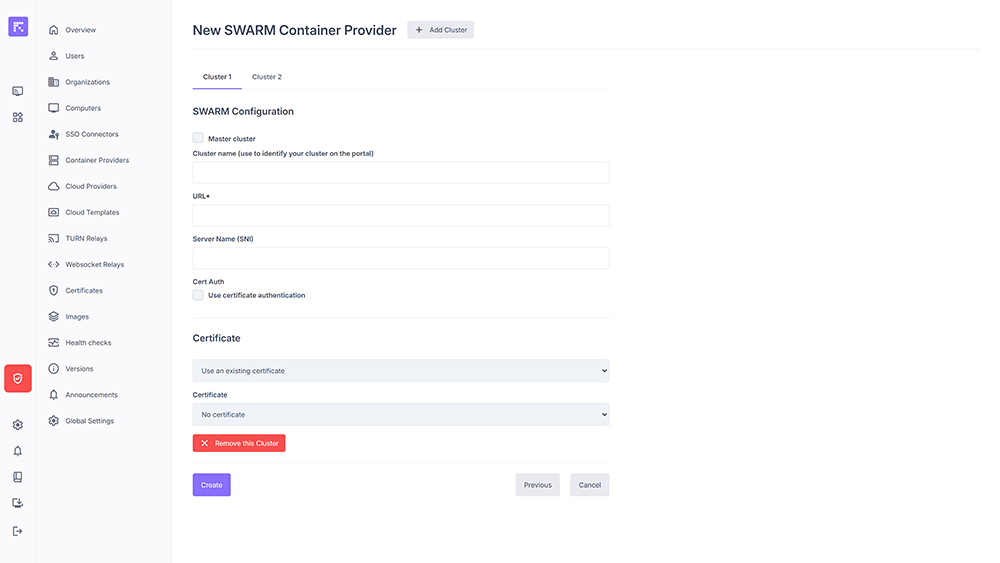
Example of a SWARM cluster configuration in multi-cluster mode¶
Add Cluster: allows adding a new cluster to the provider (option available only if multi-cluster mode is enabled).
Cluster name: internal identifier of the cluster (visible only if multi-cluster mode is enabled).
URL: API access point of the cluster. It can be an internal address or a public DNS name. In the latter case, an Ansible installation of the infrastructure will be required.
Server Name (SNI): optional field corresponding to the Common Name of the provider environment SSL certificate.
NAMESPACE: namespace used for deployments (only applicable for Kubernetes).
Cert Auth: enables certificate-based authentication, if required.
- Certificate:
Use an Existing Certificate: allows selecting an existing certificate from the Certificates module.
Specify a certificate: allows manually entering the KEY, CERT, and CA contents.
Remove the Cluster: removes the cluster (option available only if multi-cluster mode is enabled and at least 2 clusters are configured).
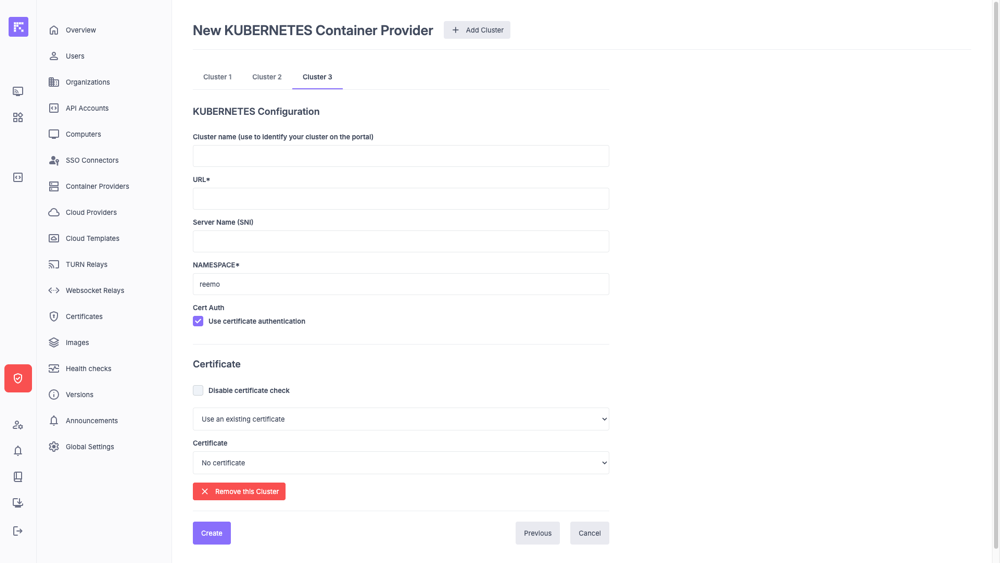
Example of a KUBERNETES cluster configuration in multi-cluster mode¶
Container Provider Overview¶
The Configuration tab displays the provider’s main settings.
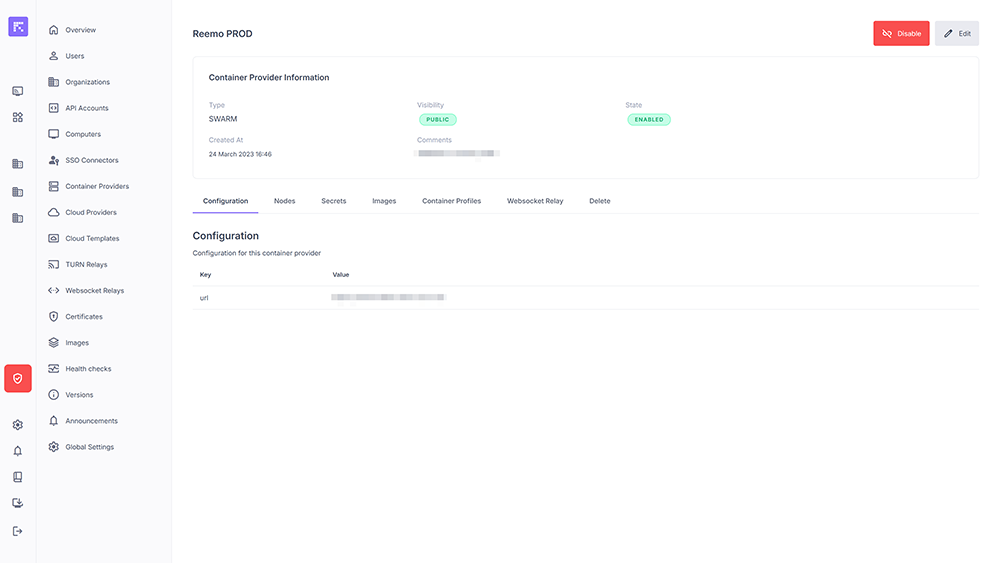
Configuration of a Container Provider¶
Node Management¶
The Nodes tab lists the nodes attached to the provider’s cluster. For each node, you will find:
IP and name.
Labels: configurable metadata (e.g., location: europe).
State: status (Ready, Down…).
Availability: Active, Pause, Drain.
Reachability: connectivity status.
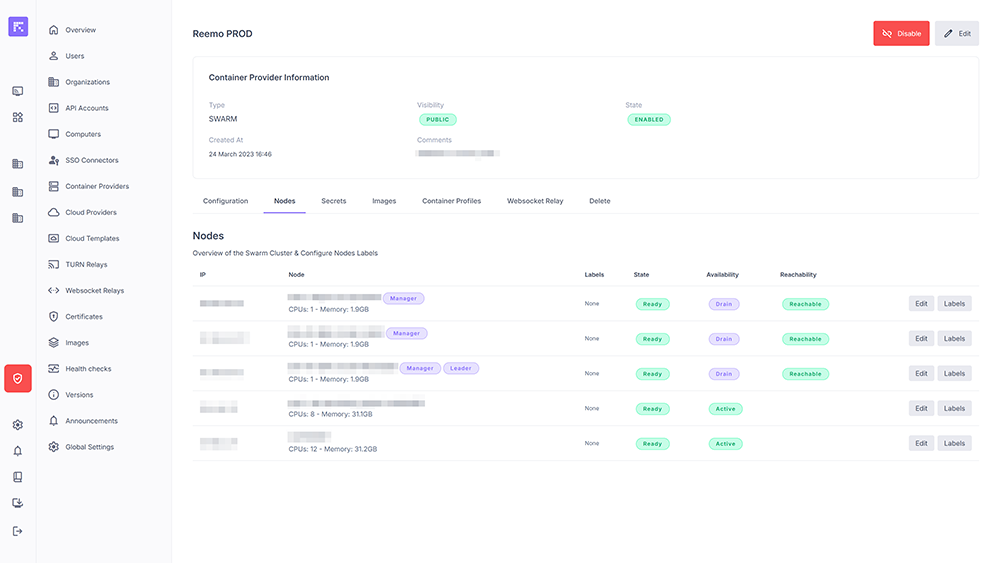
Cluster node list¶
Available actions:
Edit: change node availability.
Labels: manage custom labels.
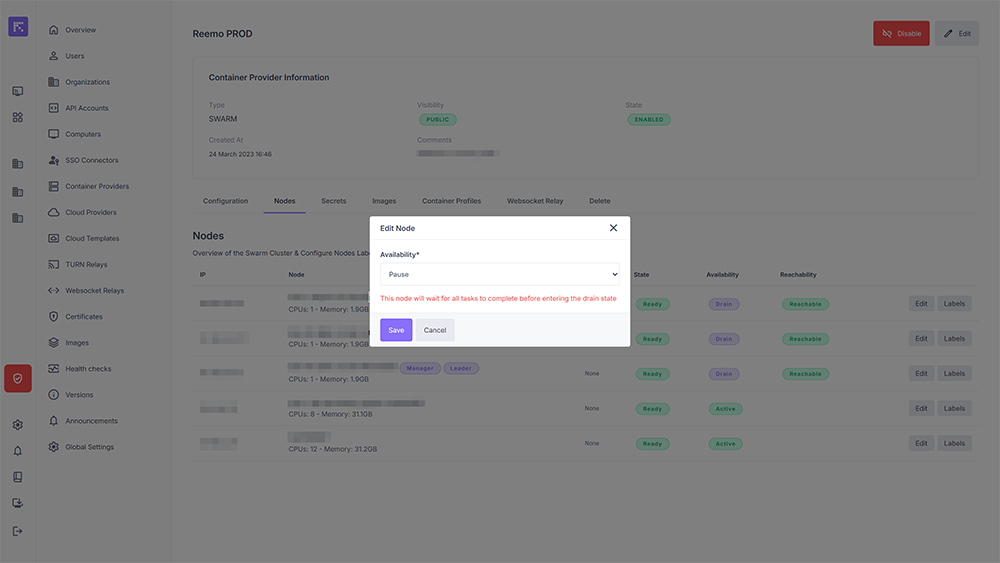
Editing node availability¶
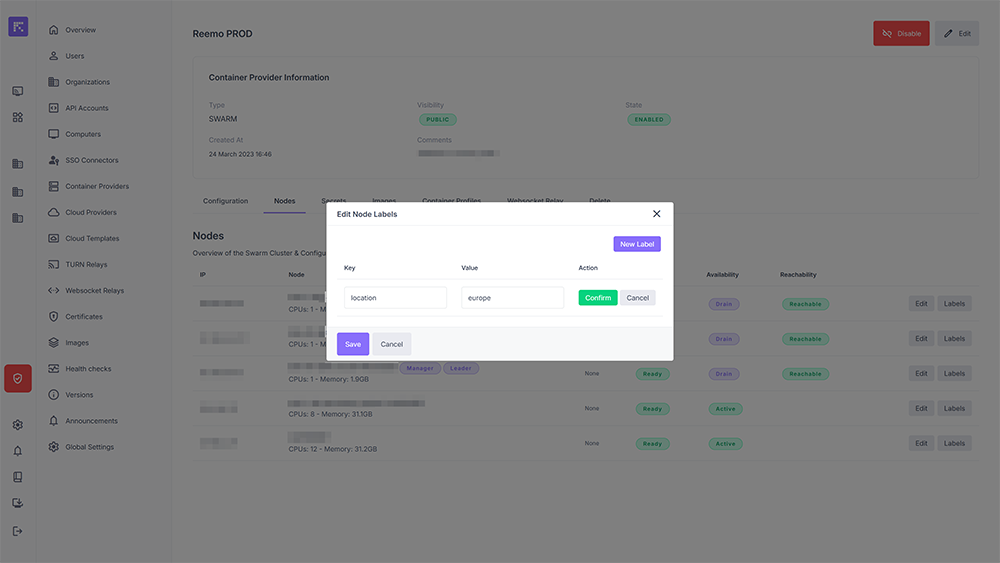
Adding or editing node labels¶
Label management works together with the Constraints system in an organization’s container profiles. For example, you could define node labels such as:
Type = NOGPU
Location = PARIS
Then, in a container profile, you could specify placement constraints:
Type EQUAL NOGPU
Location EQUAL PARIS
This ensures that all containers from that profile are deployed on nodes matching these constraints.
Secret Management¶
The Secrets tab centralizes management of Docker Secrets associated with the provider. They can be used by containers or services.
Each secret includes:
Creation date.
Unique ID.
Logical name.
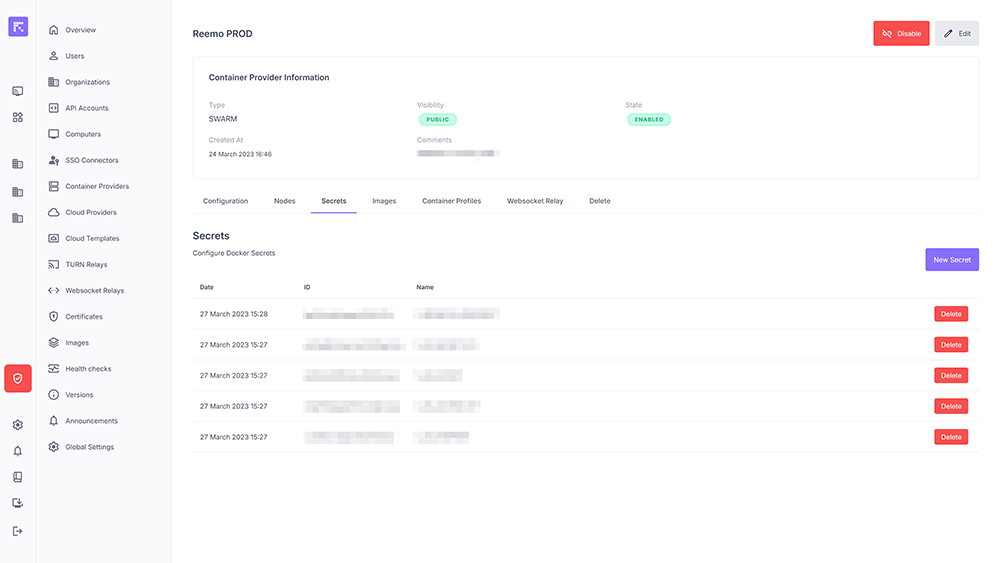
Managing provider secrets¶
Image Management¶
The Images tab allows declaring and enabling container images usable by the provider.
For each image:
Name.
State: Enabled or Disabled.
Visibility: Public or Private.
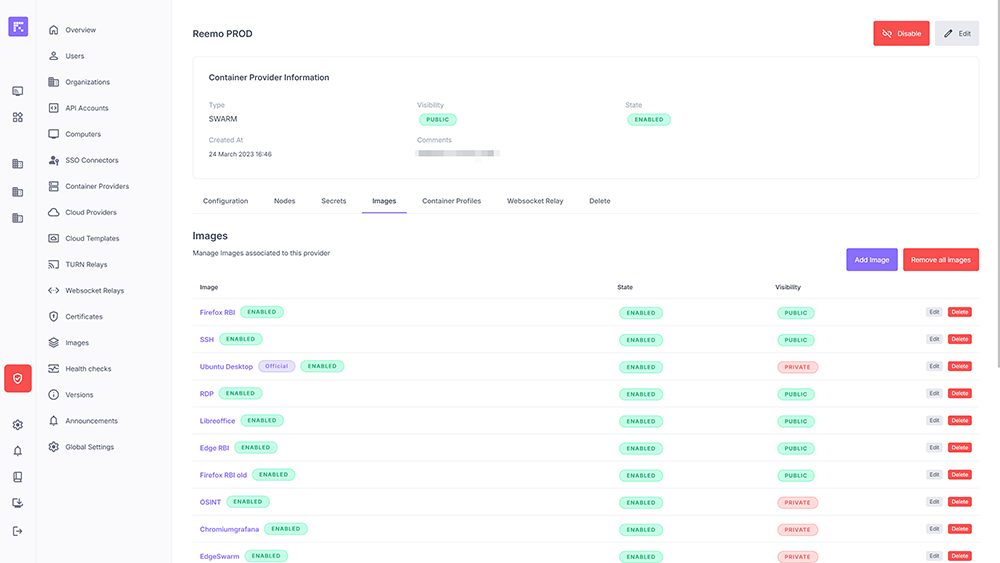
List and management of available images¶
Private Container Provider Associations¶
A Container Provider can be defined as Public or Private:
Public: automatically accessible by all organizations without additional configuration.
Private: must be explicitly associated with the organizations that need it.
This distinction makes it easy to share global resources (Public) or reserve environments for specific organizations (Private).
Managing Associations¶
From an organization’s Container Providers section, you can associate a Private Container Provider available on the platform.
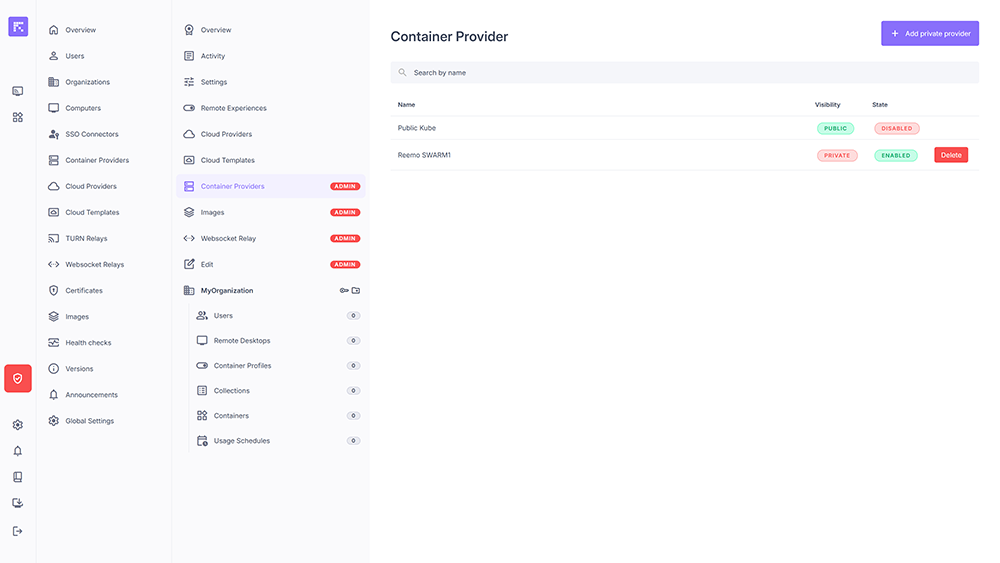
List of Container Providers associated with an organization¶
Adding a Private Container Provider¶
To associate a Private Container Provider with an organization:
Click Add private provider.
Select the desired provider from the dropdown list.
Save the association.
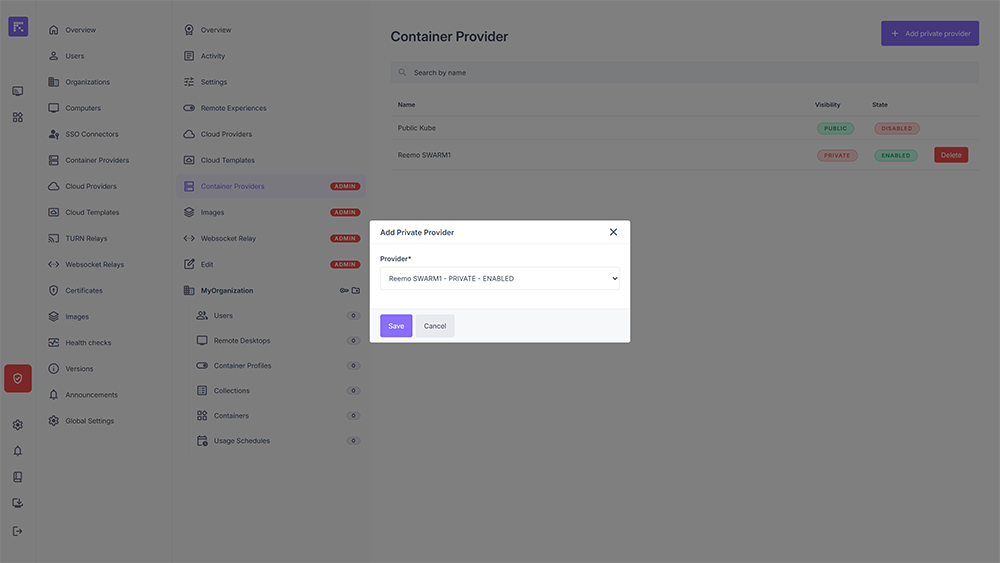
Associating a Private Container Provider with an organization¶
Multi-Clustering¶
Multi-clustering allows multiple clusters to be linked to a single Container Provider, enabling workload distribution or redundancy according to various deployment strategies.
This mechanism provides greater resilience and scalability for container environments, depending on the selected mode.
Two operating modes are available:
Mode |
Description |
|---|---|
Active / Active |
All clusters are active simultaneously. Container deployments are distributed randomly among the available clusters. This mode increases global capacity and improves load balancing across multiple environments. |
Active / Passive |
A main (Master) cluster is defined and used by default for all deployments. Other clusters are considered secondary (fallback) clusters. If the main cluster becomes unavailable, the system automatically switches to a secondary cluster to ensure service continuity. |
Note
The Active/Passive mode is particularly suitable for production environments that require high availability and strict control. The Active/Active mode, on the other hand, is ideal for scaling scenarios.
With this feature, administrators can design fault-tolerant and highly scalable container architectures, while keeping centralized management through a single Container Provider.
Summary¶
The Container Providers module offers:
Centralized configuration.
Management of nodes, images, and secrets.
Reuse of certificates for authentication and security.
Multi-cluster deployment support.
Public Container Providers are visible to all organizations.
Private Container Providers require explicit association.
This simplifies administration and strengthens consistency across container environments.