Account Settings¶
The Settings page allows you to manage and customize your Reemo account. From this space, you can update your personal information, enhance security with two-factor authentication, monitor the devices connected to your account, and review your login and activity history.
This section is organized into several categories:
Account: Update your username, email address, password, and manage your linked organizations.
Security: Enable or disable two-factor authentication (2FA) and change your password.
Active Devices: View and revoke the sessions currently associated with your account.
Authentication Logs: Review login attempts, including IP address, browser, and operating system used.
Activity Logs: Find your past sessions, their duration, and connection details.
Account¶
The Account section allows you to manage your personal information and the settings related to your user account.
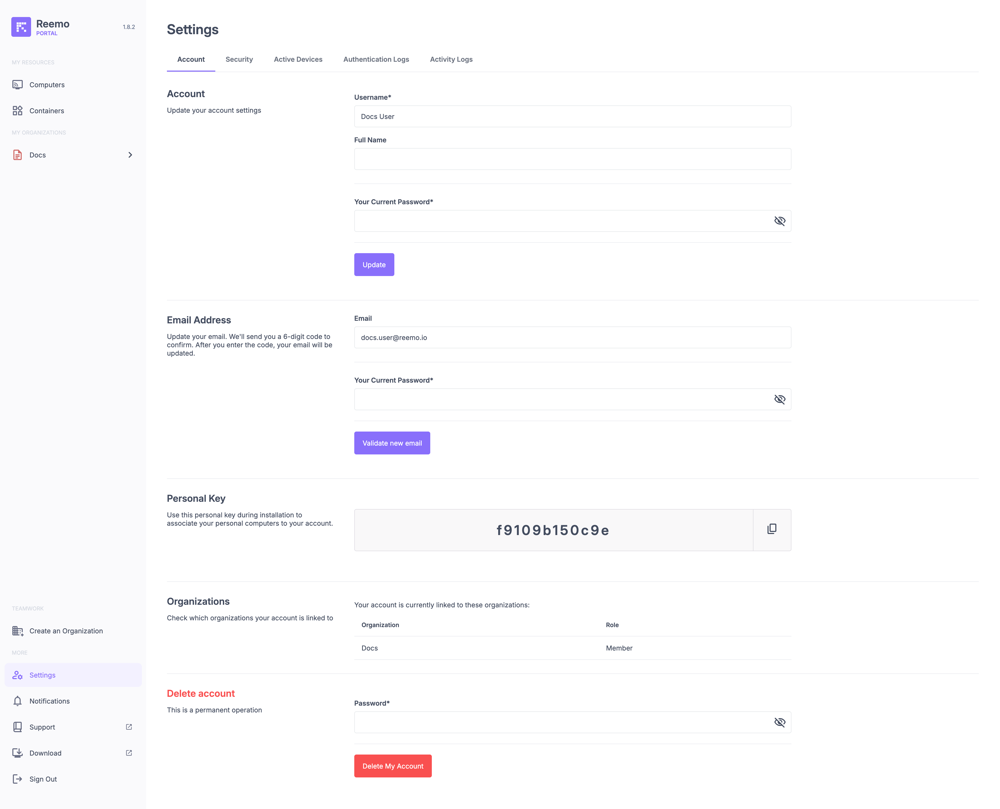
View of the Account section with profile information, email verification, personal key, linked organizations, and account deletion option.¶
The available fields are:
Username: Username associated with your account.
Full Name: Full name of the user (optional, used as a more readable identifier).
Your Current Password: Current password required to validate any update to the information above.
A dedicated section allows you to manage your Email Address:
Email: Your login and contact email address.
When changing your email, a 6-digit verification code will be sent to the new address. You must enter this code to confirm the change before the new email becomes active. This verification step helps prevent the use of invalid or unauthorized email addresses.
Below these fields, you will also find:
Personal Key: A unique automatically generated key, used to link your personal computers to your account during installation.
Organizations: The list of organizations your account is currently attached to, with the associated role (e.g. Member, Admin, Owner).
Delete Account: Permanently deletes your account. This action requires re-entering your password.
Important
If your account is managed by an organization (managed user account), you cannot change your personal information (username, email, full name) or delete your account.
If you are an Owner of an organization, you cannot delete your account as long as you hold that role.
Security¶
The Security section allows you to strengthen the protection of your account. Two main actions are available:
Enable or disable two-factor authentication (2FA) to secure your account with an authentication app.
Change your password by entering the old password, then the new password to confirm.
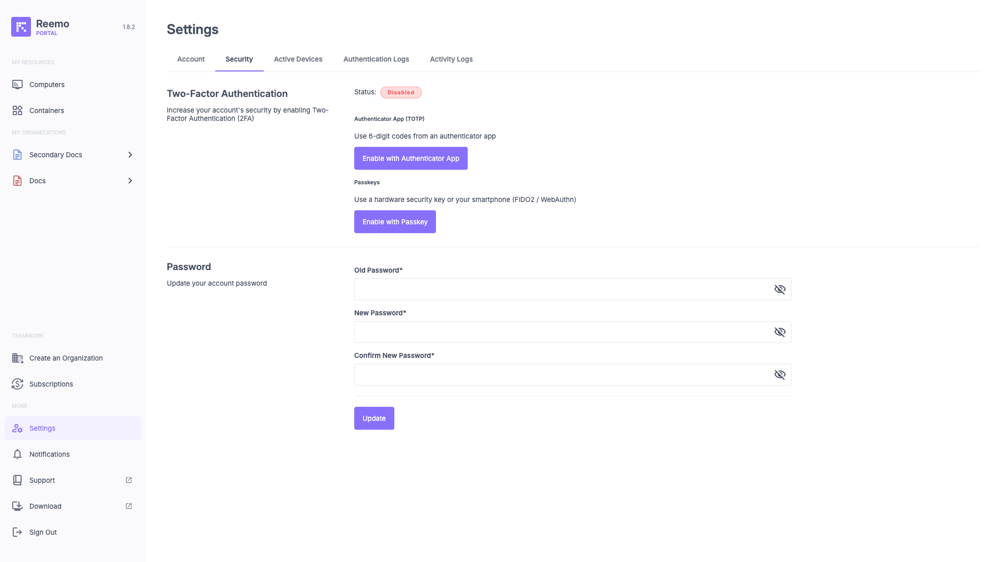
Two-Factor Authentication: Indicates whether 2FA protection is enabled or disabled.
Password: Form to update the account password.
Note
Multiple 2FA methods can be enabled simultaneously.
Authenticator App (TOTP)¶
When you choose to enable 2FA with an Authenticator App, a sub-page appears to finalize the registration of your authentication device.
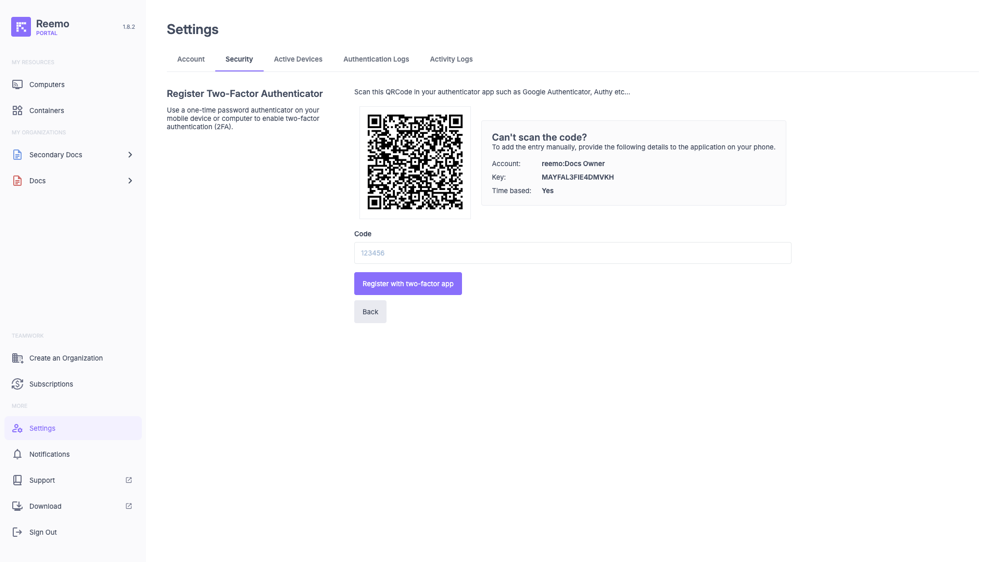
Sub-page for setting up two-factor authentication via Authenticator App.¶
Two methods are provided to link your account to an application such as Google Authenticator or Authy:
QR Code: Scan the displayed code with your authentication app.
Account + Key: If you cannot scan the QR code, manually enter the provided information (account, key, time-based code type).
Once the app is configured, enter the one-time code generated in the Code field, then confirm with the Register with two-factor app button.
Important
Two-factor authentication adds an extra layer of security to your account. Even if your password is compromised, unauthorized access will be blocked without the code generated by your authentication app.
Passkeys¶
When you choose to enable 2FA with Passkeys, a sub-page appears to finalize the registration of your authentication device.
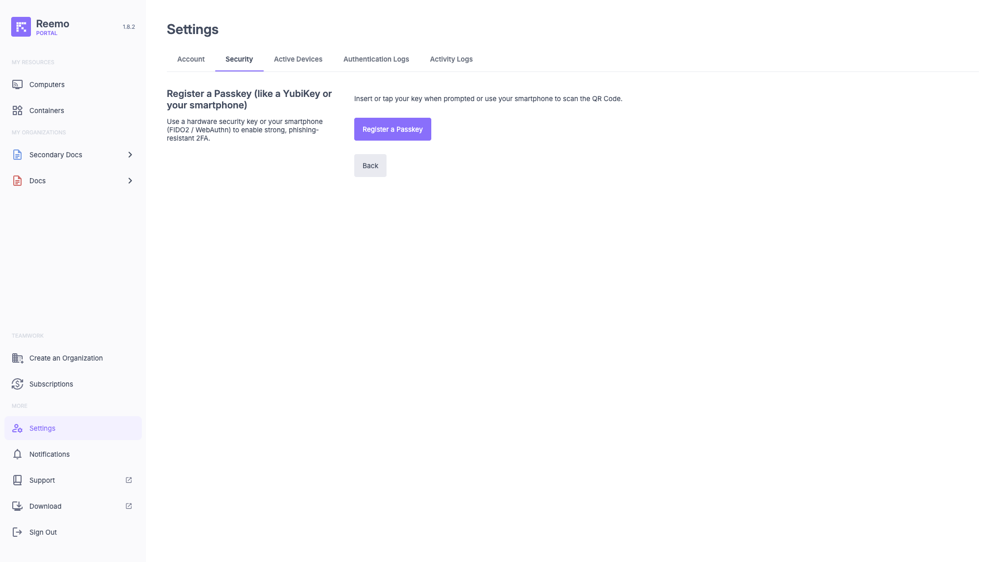
Sub-page for setting up two-factor authentication via Passkeys.¶
Follow the instructions provided by your browser to create and register a new Passkey. Once the Passkey is created, it will be securely linked to your account for future authentication.
Important
Passkeys add an extra layer of security to your account. They do not replace your password but work alongside it to provide stronger protection.
Note
Active Devices¶
The Active Devices section displays the list of browsers and devices currently connected to your account. This allows you to check your active sessions and revoke those you do not recognize.
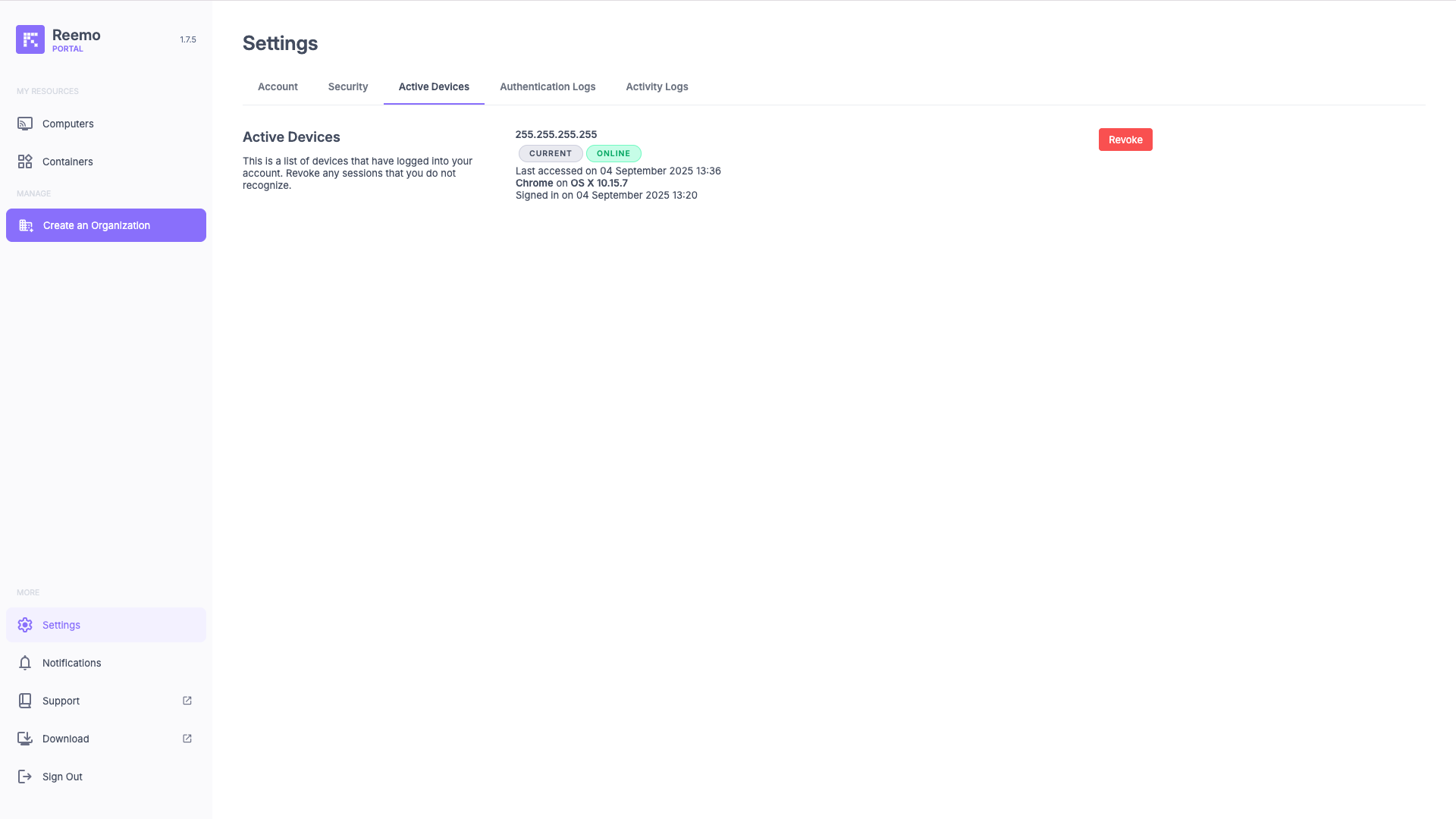
View of the Active Devices section with connected sessions, IP address, online status, and browser used.¶
The available information for each session is:
IP Address: Public IP address used for the connection.
Status: Indicates whether the session is Current and whether the device is currently Online.
Last Access: Date and time of the last activity from this browser or device.
Browser + OS: Information about the software used for the connection (e.g. Chrome on macOS).
First Connection: Date and time of the first recorded login on this browser.
A Revoke button allows you to end an active session. This action immediately disconnects the corresponding browser or device.
Note
Use this section to monitor access to your account. If you notice an unknown or suspicious session, revoke it immediately to secure your account.
Authentication Logs¶
The Authentication Logs section allows you to review the history of login attempts to your account. Each entry provides useful information to identify the origin and legitimacy of an access attempt.
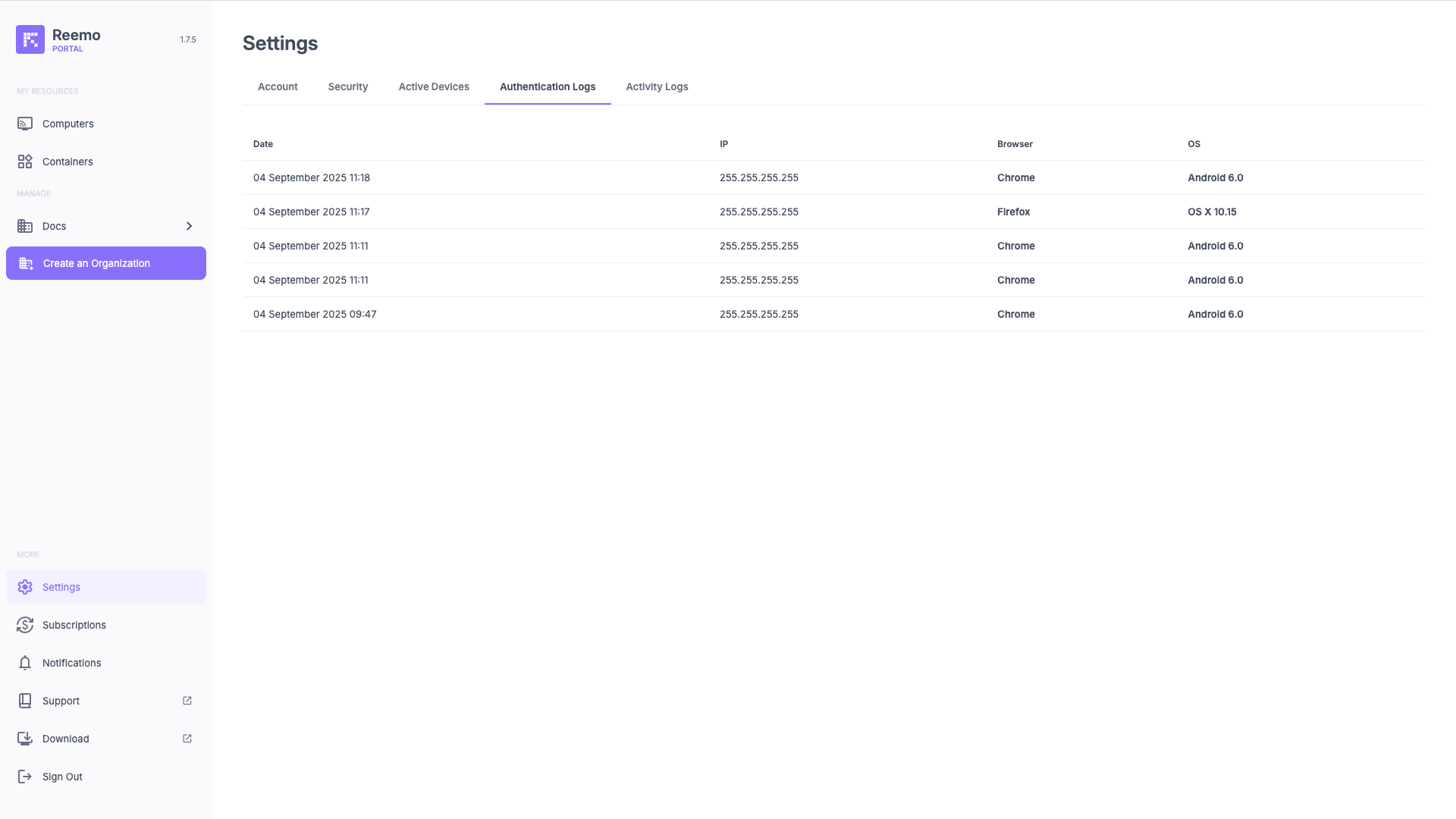
View of the Authentication Logs section showing connection history with date, IP address, browser, and operating system.¶
The available information for each authentication attempt is:
Date: Exact date and time of the login attempt.
IP: Public IP address used for the connection.
Browser: Browser used (e.g. Chrome, Firefox).
OS: Operating system used during the connection (e.g. Windows 11, OS X 10.15).
Note
This section is particularly useful for detecting suspicious logins. Regularly check the IP addresses, browsers, and operating systems to identify any unusual attempts to access your account.
Activity Logs¶
The Activity Logs section displays the history of your connections to remote computers and containers. It allows you to track your past sessions and get detailed information about their duration, the machine used, and the type of connection established.
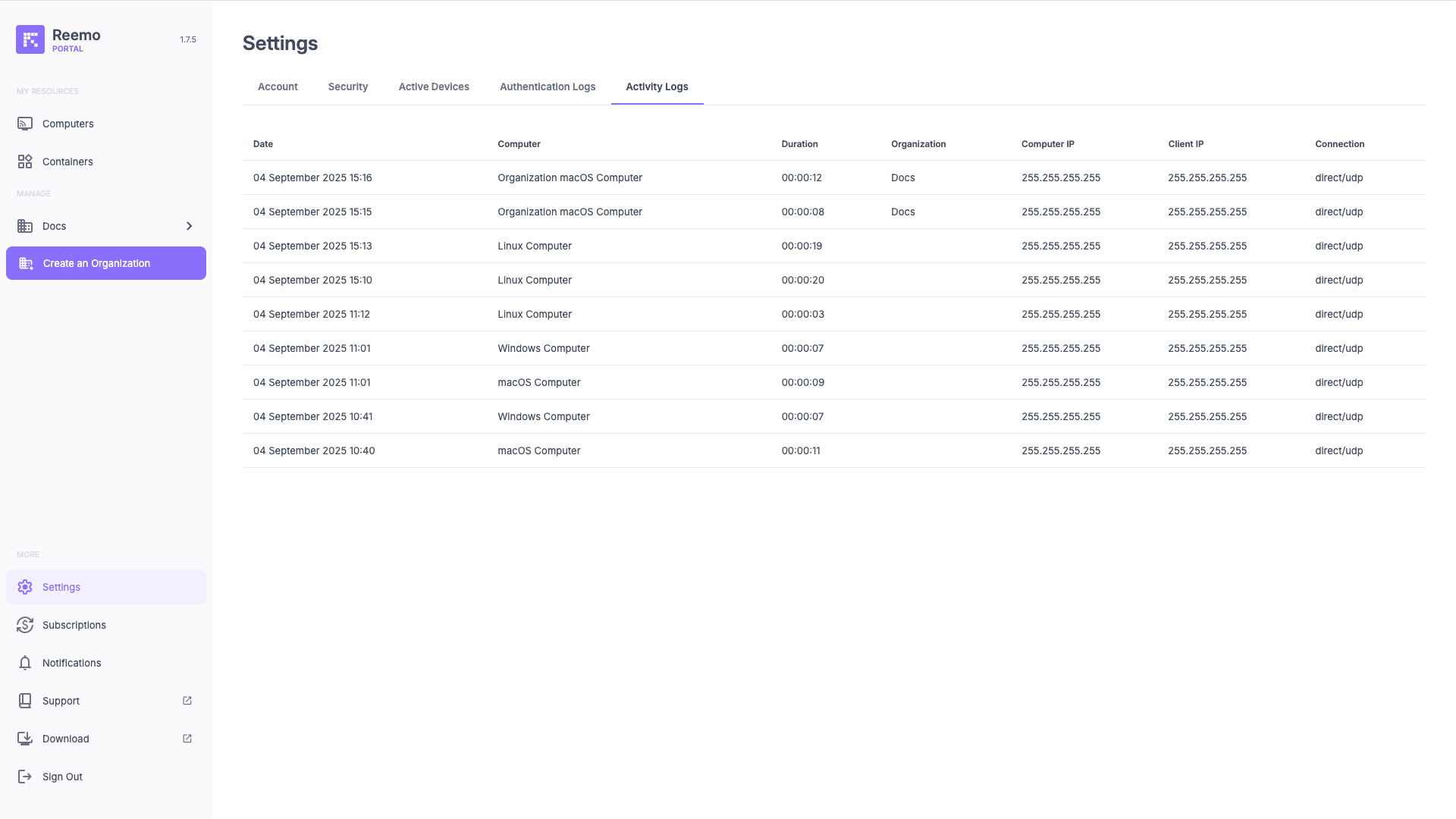
View of the Activity Logs section showing the list of sessions with their technical details.¶
The available information for each session is:
Date: Date and time of the connection.
Computer: Remote computer or container to which the session was opened.
Duration: Total duration of the remote session.
Organization: Organization the machine belongs to (empty if the machine is a personal computer).
Computer IP: Public IP address of the remote workstation.
Client IP: Public local IP address of the device that initiated the connection.
- Connection: Type of connection used:
direct/udp: Direct connection, highest performance.
relay/udp: Connection through relay, over UDP.
relay/tcp: Connection through relay, over TCP.
relay/websocket: Connection through relay, over WebSocket.
Note
This section helps you understand the quality of your connections and identify potential network issues. A direct/udp status is recommended for better performance.